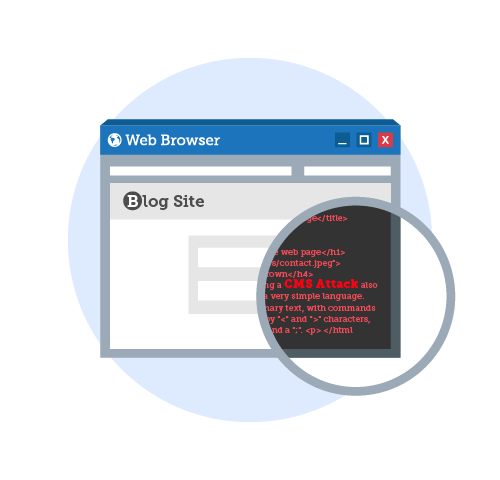
Website Defacement
Website defacement is similar to drawing graffiti on a wall, only it happens virtually. Websites’ appearance change - pictures and/or words are scrawled across the defaced website.
Why Websites are Defaced
Attackers may have different motivations when they deface a website. Political motivation is one. Attackers who are against a government or a particular movement can choose to deface related websites to air their views. Attackers who do this are known as "hacktivists". They may change the content of the defaced website with a picture or a message of their choice.
Other attackers may choose to deface a website for fun - to mock site owners by finding website vulnerabilities and exploiting these to deface the website. These attackers "taunt" the site owners. Similar to hacktivits, these attackers deface a website with a picture or a message of their choice.
In both cases, website owners face some damage to their reputation once their sites are defaced.
?
How are Websites Defaced
The most common methods of website defacements are:
- Via SQL injections - Attackers exploit a vulnerability to insert malicious SQL statements in a website.
- Via compromised content management systems - In 2013, attackers compromised numerous websites hosted on publicly available content management systems such as WordPress. The attackers compromised these sites by brute-force attack.
- By gaining access to web servers - Attackers who obtain credentials to gain access to web servers can manipulate sites/pages hosted on these web servers.
?
What Can Users Do?
IT administrators and website owners should always be ready to respond to website defacements. To prevent website defacements and other similar attacks:
- Have a backup of your site ready to help ease reverting your site to its normal state
- Employ strong passwords and account management policies to prevent unauthorized intrusions
- Check system and application vulnerabilities on critical servers including web servers
- Monitor for any unauthorized changes on critical servers such as web server, DNS server, and database servers
- Monitor for unexpected excessive load/traffic to web server & DNS servers
- Monitor for new webpage setup or new URL path accessed
- Monitor for signs of communication with command & control servers from within your network