TROJ_ARTIEF.EDX
RTF:CVE-2010-3333 [Expl] (Avast); Exp/20103333-A (Sophos)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
Spammed via email
This Trojan arrives as an attachment to email messages purportedly promoting Tibetan culture. It drops a file that is a backdoor and is infected by a file infector.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
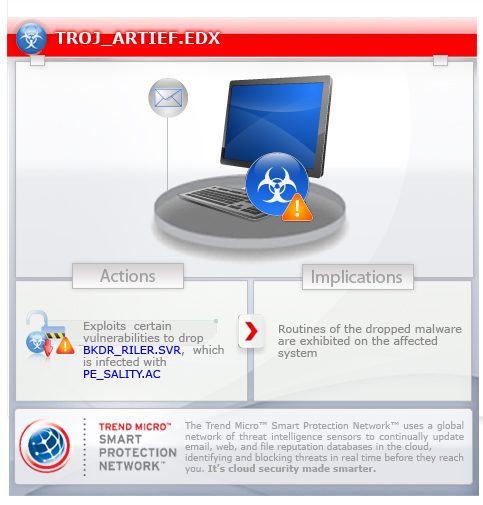
This Trojan arrives as an attachment to email messages spammed by other malware/grayware or malicious users.
It executes the dropped file(s). As a result, malicious routines of the dropped files are exhibited on the affected system.
TECHNICAL DETAILS
1,780,792 bytes
RTF
06 Apr 2012
Drops files
Arrival Details
This Trojan arrives as an attachment to email messages spammed by other malware/grayware or malicious users.
Installation
This Trojan drops the following non-malicious file:
- %User Temp%\document.doc
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003.)
Dropping Routine
This Trojan drops the following files:
- %User Temp%\svchost.exe - detected as BKDR_RILER.SVR
It takes advantage of the following software vulnerabilities to drop malicious files:
It executes the dropped file(s). As a result, malicious routines of the dropped files are exhibited on the affected system.
NOTES:
Upon execution, it opens its dropped non-malicious .DOC file %User Temp%\document.doc in order to hide its malicious routines from the user.
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003.. %Temp% is the Windows Temporary folder, which is usually C:\Windows\Temp or C:\WINNT\Temp.)
The following dropped malicious file is also found to be infected by PE_SALITY.AC:
- %User Temp%\svchost.exe - detected as BKDR_RILER.SVR
(Note: %User Temp% is the current user's Temp folder, which is usually C:\Documents and Settings\{user name}\Local Settings\Temp on Windows 2000, XP, and Server 2003.. %Temp% is the Windows Temporary folder, which is usually C:\Windows\Temp or C:\WINNT\Temp.)
Consequently, routines of both BKDR_RILER.SVR and PE_SALITY.AC are executed on the affected system.
SOLUTION
9.200
8.890.09
06 Apr 2012
8.893.00
08 Apr 2012
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you to allow full scanning of your computer.

