Ransomware Recap: Business as Usual after WannaCry Surge
 After the Week of WannaCry, the ransomware scene looks to be going back to normal, with the persistent ransomware known as Cerber (Detected by live casino online as RANSOM_CERBER family) jumping back in the limelight—this time using the that was discovered in early 2017.? The campaign involved the use of botnets sending malicious spam emails loaded with Rich Text Format (RTF) files with.doc extension contained inside zip attachments. The?RTF?files tries to exploit the , remote code execution vulnerabilities in the Windows Object Linking and Embedding (OLE) interface of Microsoft Office that was . These vulnerabilities are also currently being exploited by the notorious?DRIDEX banking trojan.
After the Week of WannaCry, the ransomware scene looks to be going back to normal, with the persistent ransomware known as Cerber (Detected by live casino online as RANSOM_CERBER family) jumping back in the limelight—this time using the that was discovered in early 2017.? The campaign involved the use of botnets sending malicious spam emails loaded with Rich Text Format (RTF) files with.doc extension contained inside zip attachments. The?RTF?files tries to exploit the , remote code execution vulnerabilities in the Windows Object Linking and Embedding (OLE) interface of Microsoft Office that was . These vulnerabilities are also currently being exploited by the notorious?DRIDEX banking trojan.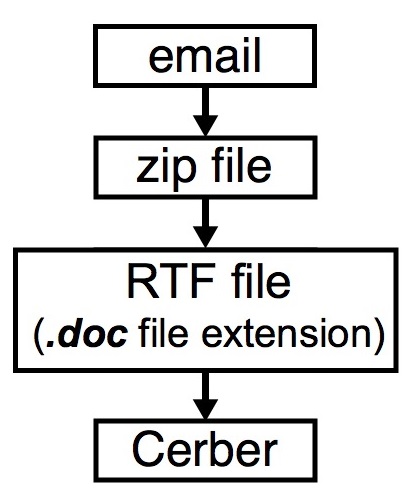
Figure 1: Cerber’s new distribution method
The ransom note for this variant comes in three forms: a text file, an image file, and an HTML Application (HTA) file.
Fake “WannaCry”
It’s been a couple of weeks since the peak of WannaCry (Detected by live casino online as?RANSOM_WANA.A?and?RANSOM_WCRY.I), but a few ransomware in circulation are still trying to take advantage of WannaCry’s high visibility.
Unlike the actual WannaCry ransomware, which had tremendous impact in terms of both scope and reach, fake WannaCry variants do much less, if any, damage. One such “ransomware” (Detected by live casino online as Ransom_FAKEWCRY) discovered in May is a Microsoft Intermediate Language (MSIL) compiled executable that only contains codes for the ransom note. It does not actually encrypt anything nor does it lock the system. Instead, it will just display a ransom note that looks similar to the one used by the real WannaCry. The ransom demand for this variant is $300:
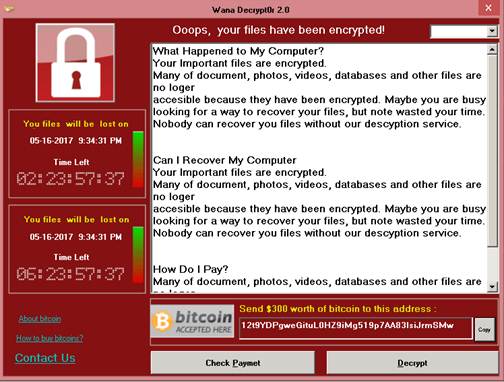
Figure 2: “WannaCry” ransom note
Despite the lack of a malicious payload, this kind of scam can trick users into paying the ransom demand, especially if they are unaware of the real differences between the actual WannaCry ransomware and its copycats.
FrozrLock
FrozrLock (Ransom_FROZRLOCK) is a platform being peddled on the dark web for a relatively affordable amount of $220 in bitcoin. Potential clients who are interested in using FrozrLock must register on a specific website to obtain an account, after which they will have access to a ransom builder interface where they can customize certain aspects of the ransomware according to their specifications: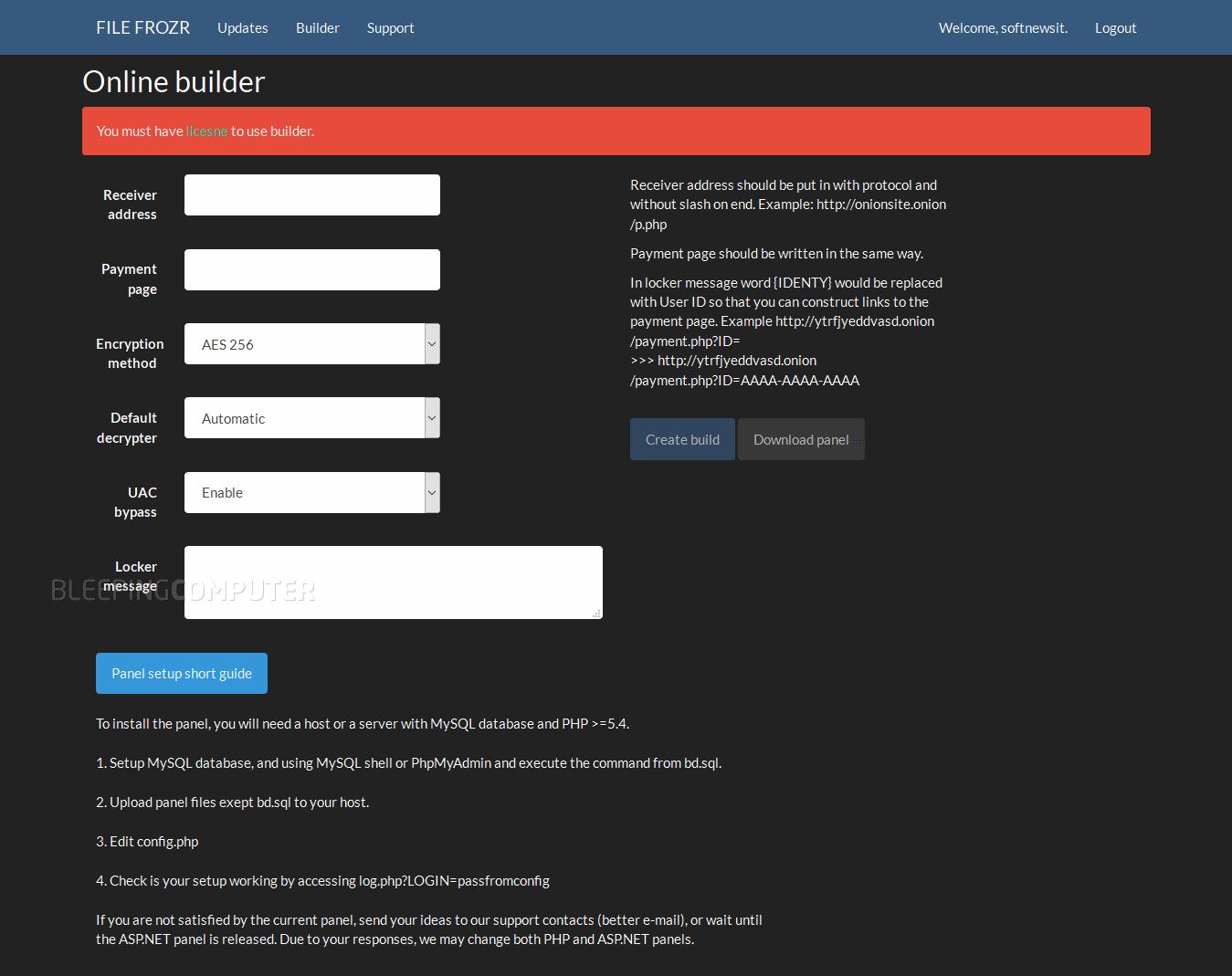
Figure 3:FrozrLock builder interface (Image courtesy of )
FrozrLock’s features include obfuscation with a renamed ConfuserEx 1.0 as well as the ability to delete shadow copies. In addition, it uses Windows' cipher.exe with parameter /w to swipe free disk space to prevent restoration of deleted shadow copies.
XData
Ukraine has been a recent target of a new ransomware called XData (Detected by live casino online as Ransom_SOREBRECT), which quickly spread throughout the country—locking systems and encrypting shared file using the PSEXEC tool.
While, XData’s distribution method is still unclear, 95% of its victims have come from Ukraine, with some scattered reports about infections from Germany, Russia and Estonia. Once XData gains access to a user’s system, it will use the AES algorithm to encrypt files with the .~xdata~ extension. The files encrypted by XData will have no way of decryption without the victim paying the ransom:
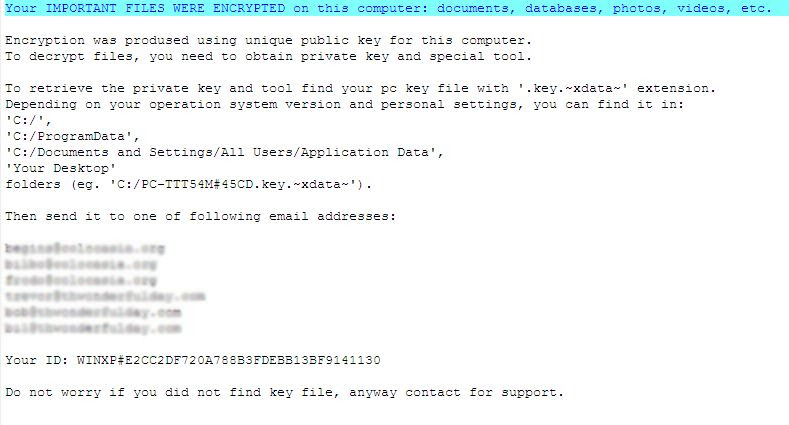
Figure 4: XData ransom note
Although the ransomware stories for this week lack the hype seen during WannaCry’s peak, it goes to show that the ransomware threats are as varied as they are numerous. Familiar ransomware like Cerber continue to evolve, while new variants hit the scene. WannaCry served as a wake-up call for the public, and vigilance must be maintained to defend against these malware, as lesser-known ransomware can be just as effective and dangerous as high profile ones.
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as?live casino online? Deep Discovery? Email Inspector?and?InterScan? Web Security?prevents ransomware from ever reaching end users. At the endpoint level,?live casino online Smart Protection Suites?deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat.?live casino online Deep Discovery Inspector?detects and blocks ransomware on networks, while?live casino online Deep Security??stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses,?live casino online Worry-Free Services Advanced?offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users,?live casino online Security 10?provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our?free tools?such as the?, which is designed to detect and remove screen-locker ransomware; as well as?, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Ultime notizie
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One?
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One? Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks