TROJ_WORID.A
Trojan.Win32.Jorik.Skor.oa (Kaspersky); Downloader-CEW.ai (McAfee)
Windows 2000, Windows XP, Windows Server 2003


Threat Type: Trojan
Destructiveness: No
Encrypted: Yes
In the wild: Yes
OVERVIEW
This Trojan has received attention from independent media sources and/or other security firms. Specifically, it arrives via SQL injection in order to compromise sites from from various industries. It is found that a malicious server tries to inject sites with a .PHP script that is housed in a site called LizaMoon.
To get a one-glance comprehensive view of the behavior of this Trojan, refer to the Threat Diagram shown below.
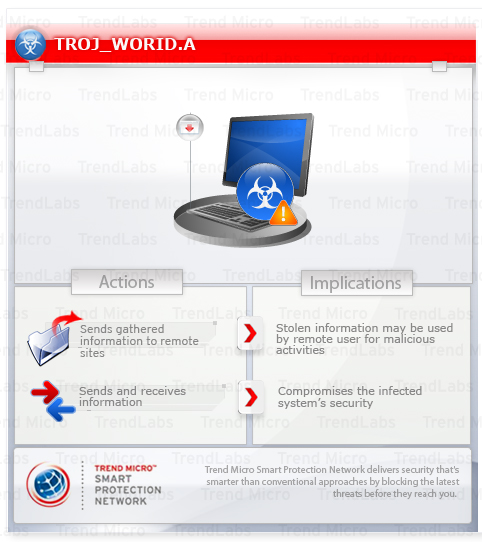
It may arrive when a user accesses a compromised website.
It reports system infection to certain websites, along with gathered information about the infected system.
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
It connects to certain websites to send and receive information. It deletes itself after execution.
TECHNICAL DETAILS
71,680 bytes
EXE
Yes
31 Mar 2011
Collects system information, Compromises system security
Arrival Details
This Trojan may be unknowingly downloaded by a user while visiting malicious websites.
Other System Modifications
This Trojan adds the following registry entries:
HKEY_CURRENT_USER\Software\Microsoft\
Windows\CurrentVersion\Internet Settings\
Zones\{random character}
1806 = "0"
Other Details
This Trojan connects to the following website to send and receive information:
- http://{BLOCKED}ssmortgages.in/djcash.php
- http://{BLOCKED}um.in/djcash.php?
It deletes itself after execution.
NOTES:
It reports system infection to the above-mentioned sites by sending encrypted data using the following parameters:
- ini={encrypted data}
This parameter includes the following information:- Installation date and time
- System ID
- Trojan ID
- data={encrypted data}
This parameter includes the following information:- Debug information
- Operating system
- User privelege
As of this writing, however, there is no reply from the server.
It enumerates active windows on a system and looks for windows with the string sysinternals in it. If it finds one, it does not continue its malicious routine.
SOLUTION
8.900
7.943.00
01 Apr 2011
Step 1
For Windows XP and Windows Server 2003 users, before doing any scans, please make sure you to allow full scanning of your computer.
Step 2
Delete this registry key
Important: Editing the Windows Registry incorrectly can lead to irreversible system malfunction. Please do this step only if you know how or you can ask assistance from your system administrator. Else, check this first before modifying your computer's registry.
?- In HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones
- {random character}
Step 3
Scan your computer with your live casino online product to delete files detected as TROJ_WORID.A. If the detected files have already been cleaned, deleted, or quarantined by your live casino online product, no further step is required. You may opt to simply delete the quarantined files. Please check this for more information.
NOTES:

