Microsoft Detection Tools Sniff Out Fileless Malware
 Microsoft recently reported that their advanced threat protection tools were able to detect and block two heavily obfuscated and malicious scripts. The threats were apparently using the Sharpshooter technique, which was documented and published in a from a British security firm.
Microsoft recently reported that their advanced threat protection tools were able to detect and block two heavily obfuscated and malicious scripts. The threats were apparently using the Sharpshooter technique, which was documented and published in a from a British security firm.
A from the company details the elusive payload—it did not trigger antivirus scanning, was loaded using a legitimate process that executed the scripts, and also left no trace on the disk. Given the characteristics, they classified the scripts as .
Instead, it injects malicious code into the memory of a running application or abuses legitimate tools already on the system or device.
For these detected fileless threats, the attack was done in two fileless stages, involving an elusive .NET executable payload that downloads data using DNS queries (), which is then used to initialize and decode the core of the malware. The core is also a fileless threat since it executes in the memory without writing to the disk.
In their report, they concluded that the malware was probably a testing activity, not an actual attack.
Malware detection has and is continuously keeping up with advancing threats, forcing malicious actors to look for new evasion methods and avenues of entry. Our mid-year security roundup detailed the rising number of malware that challenged file-based detection technologies. Different types stood out—small-sized malware, macro malware, and of course fileless malware.
Fileless malware have been significant threats on the security landscape for a little over a year. In June of 2017 we saw the self-destructing ; and later that year we reported on the Trojan , which was a completely fileless malware. We also noted increased security events involving these types of malware.
From the beginning of the year to June 2018, we saw a 56% increase in events blocked by live casino online products.
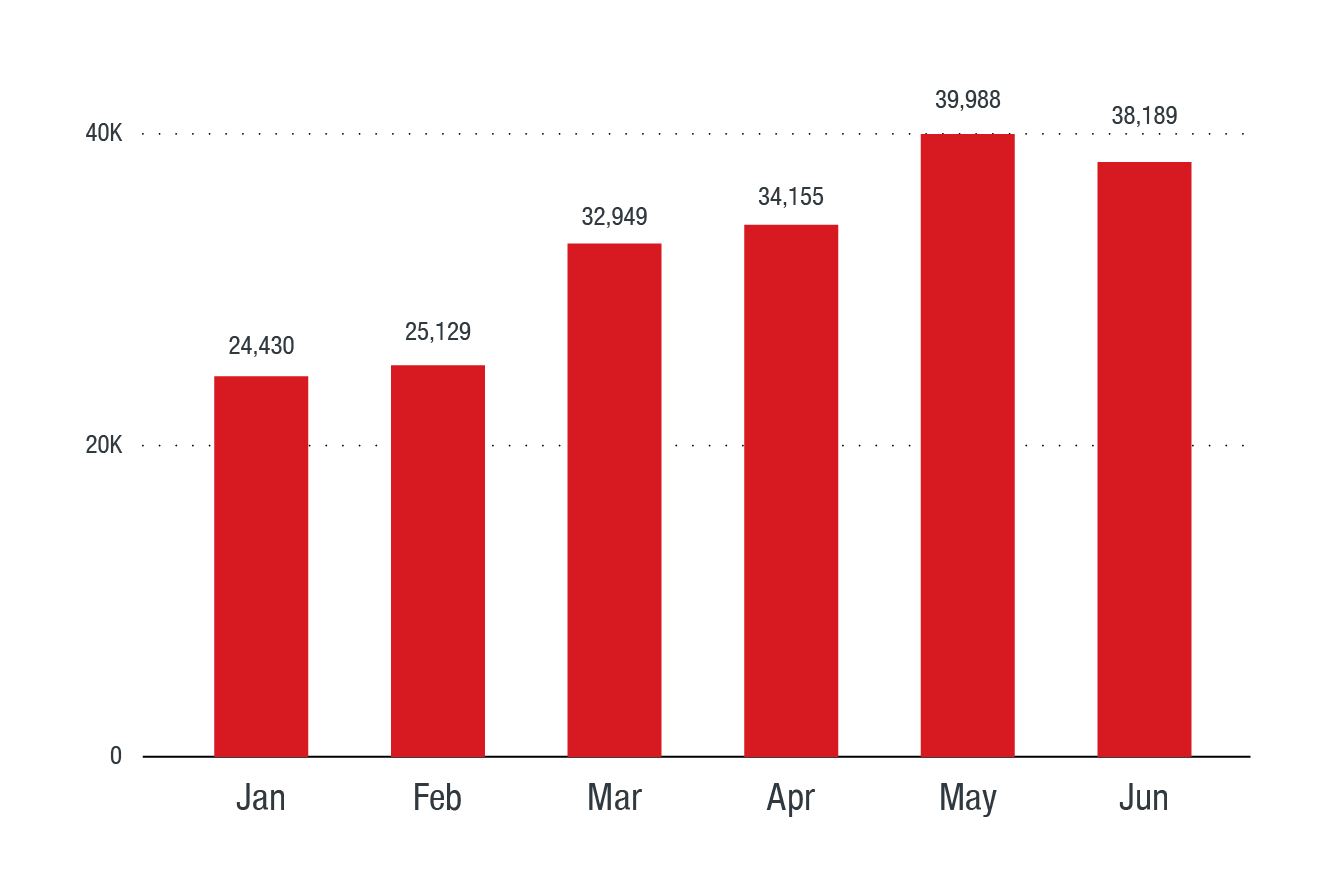
Figure 1. Fileless events blocked in the first half of 2018
A recent incident reported in July 2018 showed that malware authors continue to innovate with fileless techniques. There were reports of a fileless cryptocurrency-mining malware called PowerGhost that was targeting corporate systems. The malware took advantage of legitimate software tool PowerShell as well as the vulnerability to spread undetected across devices and servers in different organizations.
Containing the problem
Most threats are multi-component, and leave clues beyond files—emails or links from their delivery mechanisms, evidences from payloads that come via servers, or behavioral clues in network or system logs. According to Microsoft, as soon as the Sharpshooter technique became public, they knew that it would be abused and used in attacks. To detect the fileless threats, they used a multi-layered approach with their Antimalware Scan Interface (AMSI), behavior-monitoring, and boot-sector protection.
It shows that enterprises need to combat fileless threats with cross-generational security solutions and employ integrated layers of protection across the network. live casino online Smart Protection Suites deliver several capabilities like high fidelity machine learning, web reputation services, behavior monitoring, and application control, and vulnerability shielding that minimize the impact of this threat. live casino online Endpoint Sensor will also be effective in monitoring events, as this product will help quickly examine what processes or events are triggering the malicious activity.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Unveiling AI Agent Vulnerabilities Part II: Code Execution
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One?
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One? Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks